Feature Focus: Scanning Docker Images
While scanning source code of custom applications is essential, it’s not enough to guarantee the security of a containerized application. Docker images contain a vast number of Open Source components, which may represent a significant risk if not properly managed. This is why CAST Highlight has developed a new capability that allows users to scan the contents of a Docker image to identify potential risks and vulnerabilities.
Scanning Docker images for Open Source components is critical because it provides a comprehensive view of the security and compliance posture of an application. By scanning Docker images, users can identify vulnerabilities, license issues, and obsolete versions of third-party dependencies before they become a threat to the organization. CAST Highlight is now able to automatically scan Docker images. Let’s see how it works.
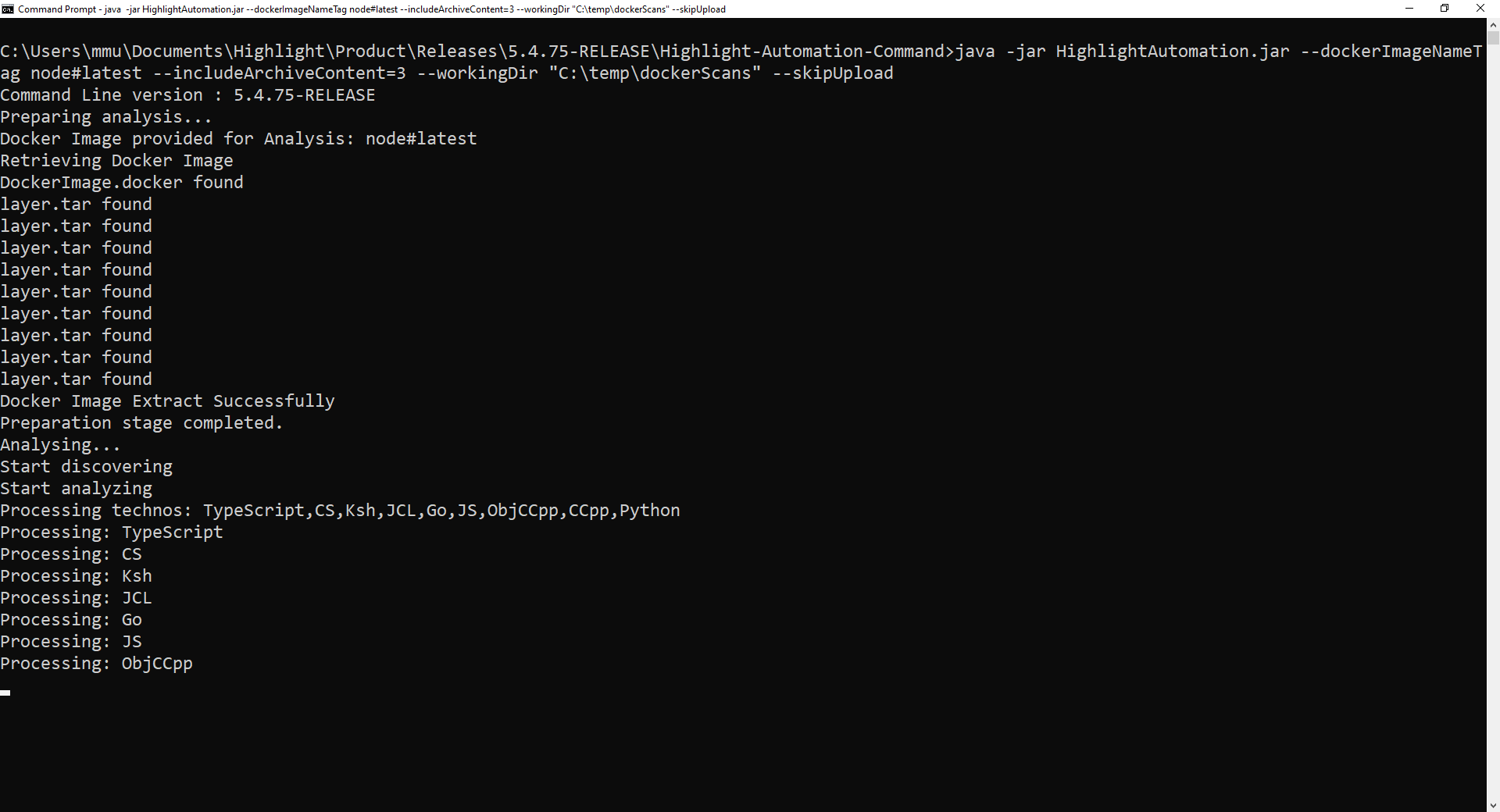
How to scan a Docker image with CAST Highlight’s command line
In the command line, there are a couple of options to include for scanning a Docker image:
- dockerImageNameTag: the name and tag of the Docker image you want to scan. Note that image name and tag should be separated by a “#” (e.g., –dockerImageNameTag node#latest)
- includeArchiveContent: the level of depth for extracting content of archive files (.jar, .zip, etc.). For Docker image scans, we recommend a depth level of 3 (e.g., –includeArchiveContent=3)
And… that’s pretty much it. The rest of the parameters are the ones you would typically use with the command line. You can also run the scan of a Docker image by using a .properties file.
Now that the command line is running, it searches first for the image locally. If it was not pulled yet on your machine, the command line automatically downloads the image from Docker Hub.
Then, the command line saves the image as an archive (DockerImage.docker file) on your file system so that it is accessible outside the Docker environment. If a Docker image is composed of different layers stored as .tar files, this is where the –includeArchiveContent parameter comes into the play. By adding this option with a level of depth at 3, the command line will recursively extract the content of archives three times, which is the right level of depth to get interesting results for most Docker images. Don’t hesitate to adjust this value for your needs, while keeping in mind that the more depth, the more time the scan will take.
Once the required archive content has been extracted, the command line starts the discover and scan steps as usual. The final step is the deletion of extracted content so that your hard drive stays lean 😊
Requirements & limitations
- CAST Highlight’s Command Line version 5.4.75 or higher
- Docker Desktop installed and running
- Access to internet for distant Docker images (i.e., not local to your machine)
- For Linux, local image scan is not possible, it should be distant
- Images with symbolic links are not supported (i.e., all files should be physically present on the machine where the scan happens)

