Feature Focus: Preventing the Use of Risky OSS Components Across the Enterprise
How to search for a component?
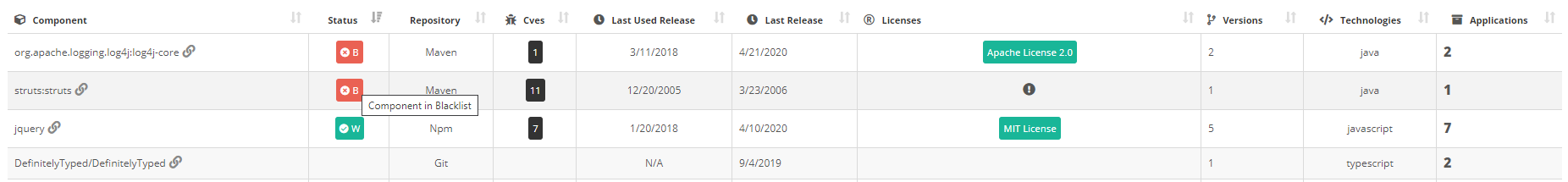
Prior to establishing your list of approved/denies OSS components, you need to identify them in the CAST Highlight SCA database. The new Component Catalog feature in CAST Highlight allows you to search for a third-party component in our SCA database which is now made up of 118+ million components. You can then assign it to a approved or denied. Below are the different search methods and options:
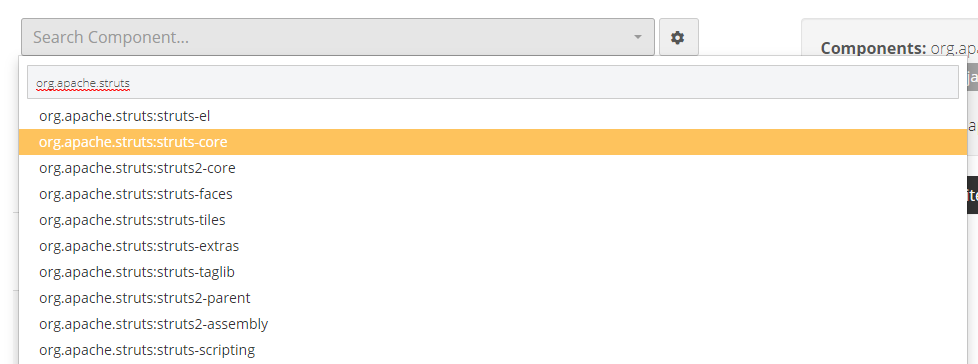
- Search by component name: when you start typing the name of the component you’re seeking, CAST Highlight returns a list of known components matching your keyword. The more you type, the more specific the results will be.
- Refine the search with some options: in order to further refine the returned component list, you can add search criteria
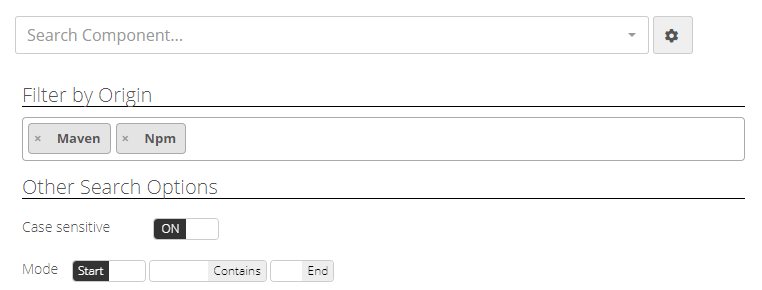
- Filter by origin: select the Open Source forges if you know where the component you’re seeking is located (Maven, NPM, Github, NuGet, GitLab, PyPi, Packagist, RubyGems, etc.)
- Enable/Disable case sensitivity: some Open Source forges (e.g. NuGet for .Net packages) may have components with specific uppercase and/or lowercase characters.
- String position mode: select whether the keyword you type starts, ends or is contained within the component name you’re seeking.
- Search with a local file: this search method is probably the most accurate as it relies on the unique fingerprinting mechanism of third-party artifacts (CAST Highlight currently references 11+ billion unique fingerprints). Simply select one file from the component, CAST Highlight will automatically display the component corresponding to the fingerprint you submitted.
Note that there is no file upload to the platform. When selecting a file from your computer (typically a JAR, a DLL, one of the source files, etc.), your browser computes its SHA256 fingerprint locally and sends this unique fingerprint to the platform to verify if it matches one of the fingerprints we have today in our SCA database. The SCA database then returns the corresponding component with its meta data (license, known vulnerabilities, versions, etc.).
Build and manage your list of approved/denied third-party components
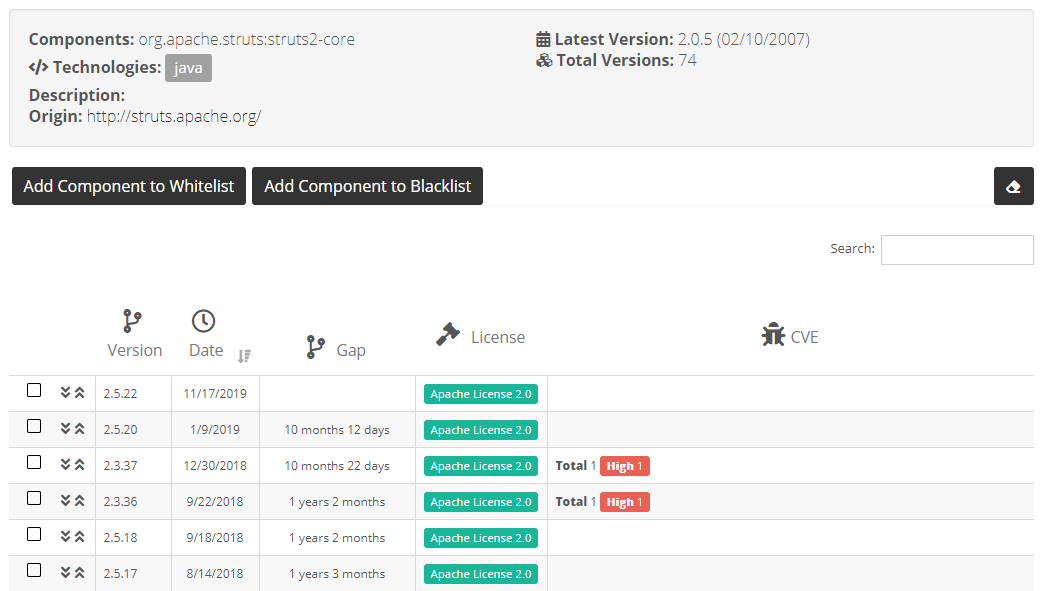
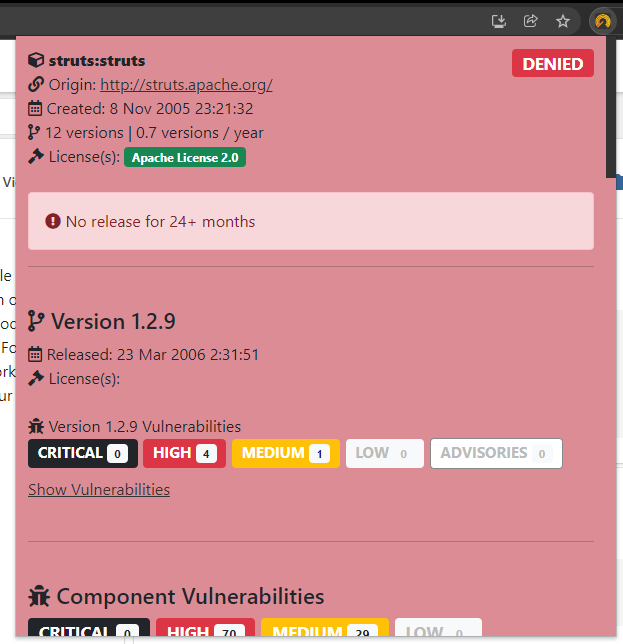
Once you have found the component you were seeking, you can now visualize its metadata (licenses, possible vulnerabilities, version timeline, description, etc.) to decide whether it will be part of the approved/safe or denied/unsafe component list for the portfolio:
- If you want to mark a whole component as denied, simply click on “Add Component to Deny List”. It will be added to the component table to the left.
- Conversely, if you want to mark a whole component as approved, click on “Add Component to Approved List”.
- You can also select one or more specific versions for this component to be appproved or unauthorized. Check the version boxes and click on “Add Selection to Approved List/Denied List”.
- It is also possible to include a specific version in a list and all older versions, or all newer versions. This is particularly useful when a component has a significant change across versions (e.g. versions below 3.2.0 are vulnerable but newer versions are safe).
- Note that these lists of allowed/denied components must be set at the root-level of the portfolio (i.e. not on sub-domains)