Feature Focus: How to manage third-party components and vulnerabilities in SCA results
Vulnerability “New” Status
CAST Highlight’s SCA database is made up of 118+ million Open Source components gathered from various forges that we crawl such as Github, GitLab, Maven Central, NPM, NuGet, RubyGem, Packagist, etc. Depending on the component name and version detected in an application scan, CAST Highlight finds possible vulnerabilities (CVEs) by cross-referencing the National Vulnerablity Database (NVD) from NIST, across 150+ thousand known vulnerabilities (our vulnerability database is synced every hour for new or updated entries). Users typically run a first analysis of their application to establish a CVE baseline and prioritize risk mitigation actions.
CAST Highlight recently released a CVE status flag to help users quickly identify vulnerabilities that have been newly introduced in a new scan. The count of new CVEs can be easily seen in a blue pill on top of the total count to date of each criticality level.
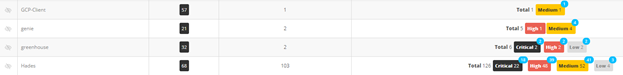
- At the portfolio level for each application: easily identify “stable” applications that are less risky for your organization
- At the application level for each component: quickly see components that should have your attention as they are introducing new vulnerabilities into your application
- From the API: extract this CVE status information (“isNew”: true) by pulling application details with the following call: WS2/domains/{domainId}/applications/{applicationId}
Vulnerability (CVE) Exclusions
In some cases, these possible vulnerabilities may not be relevant in the application results after the application teams take a deeper look. Hence it is now possible to exclude vulnerabilities from the application for the following reasons:
- This CVE has been patched already
- This CVE can’t be exploited in the context of the application
- This CVE is incorrectly associated with the third-party component (CVE false positive)
- The Third-party component is incorrectly associated with the application (component false positive)
- Other
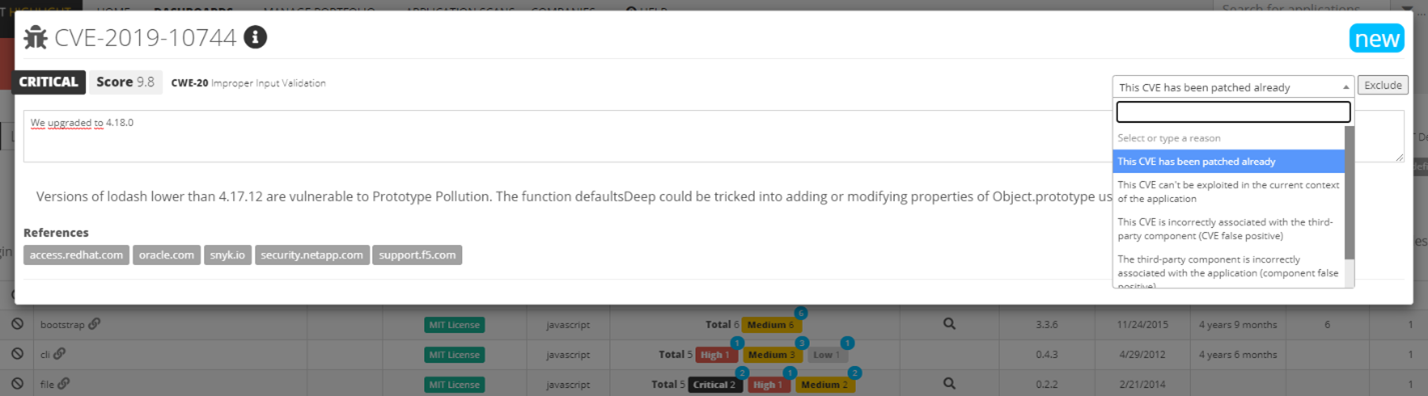
Finally, click on “Exclude” to see the number of CVEs automatically reduced.
Exclusions are regularly extracted in an anonymized list by the product team to proactively improve our CVE matching algorithm and remove possible false positives from all CAST Highlight instances.
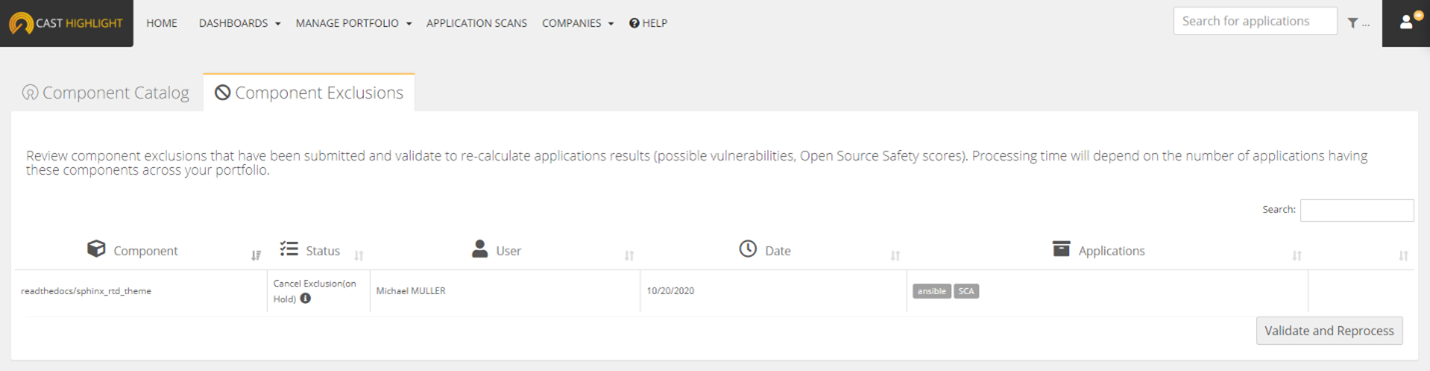
Roles & Exclusion Logs
All user roles (Portfolio Managers, Application/Domain Contributors) can exclude a CVE, except Result Viewers.
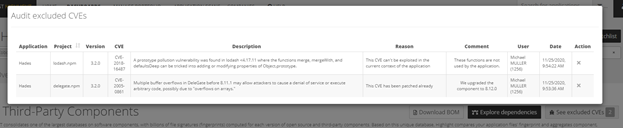
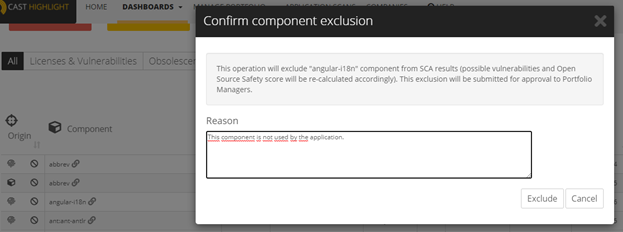
Component Exclusions
The same way a CVE can be excluded, users can request the exclusion of a component that may have been incorrectly detected by CAST Highlight. This may happen in the case when the original component is not available on the Open Source forges we crawl (Maven, Github, NPM, etc.). As a result, (see how component detection works in this article), CAST Highlight displays the oldest matching occurrence in the SCA database. In most cases, this happens for system libraries and proprietary or deprecated components.