SCA – Change in CAST Highlight Code Reader & CLI: Dependency Detection Defaults
What’s Changing?
- Today (current behavior): The CLI detects OSS components both by analyzing package manager files (e.g.,
pom.xml,package-lock.json,yarn.lock, etc.) and by fingerprinting individual files using their SHA256 signature. - With the new version (default behavior): Code Reader and CLI will only retain dependencies declared in package manager files. This means detection will primarily reflect the components your applications explicitly reference. Note that fingerprints from .jar, .dll, and .min.js will still be resolved.
What If You Still Want File Fingerprinting?
If you prefer to continue detecting OSS components via file signature analysis (SHA256 fingerprinting), you can easily do so by running scans with the new option:
This ensures that your scans include both:
- Dependencies declared in package manager files, and
- Components identified through file fingerprinting.
Balancing Accuracy and Coverage
By defaulting to package manager–based detection, your scan results will typically include fewer false positives, since only explicitly declared dependencies are retained. The trade-off is that some OSS usage may go unnoticed — for example, when developers directly copy/paste third-party source files or manually add external libraries without updating package manager files. Ultimately, it’s up to you to configure your scans based on your organization’s goals: prioritize clarity and accuracy by sticking with the default, or maximize coverage by enabling fingerprinting with --fingerprints.
Why This Change?
- Clarity: Package manager–based detection aligns results with the dependencies that your teams explicitly declare and manage.
- Performance: Scans run faster and generate leaner results without unnecessary noise.
- Flexibility: You remain in control — file fingerprinting remains available via the
--fingerprintsflag.
How to Prepare
- Review your current usage of the Code Reader and CLI.
- If your workflows depend on file fingerprinting, update your scripts or pipelines to include the
--fingerprintsoption. - If you rely primarily on package manager detection, no action is needed.
👉 This change will be available in the as of version 5.10.8 of the CLI, version 1.2.18 of the Code Reader, so we recommend updating your scanning processes in advance to avoid surprises.
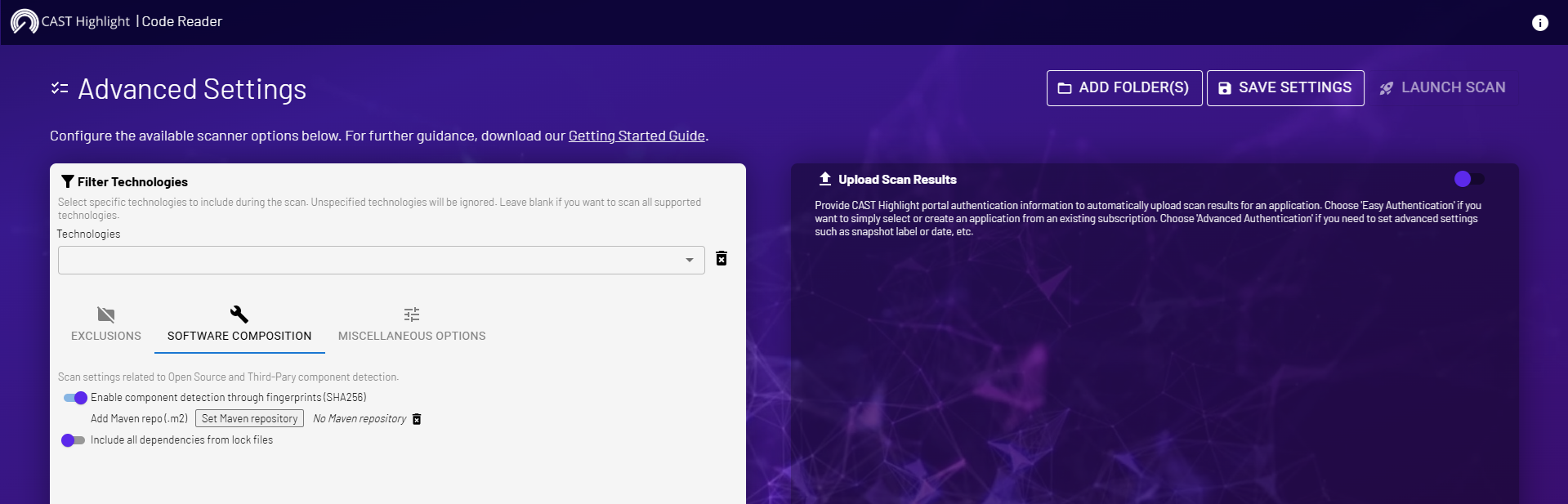
If you’re using the Code Reader, this option is available from ADVANCED SETTINGS, under the Software Composition tab. Switch on the option ‘Enable component detection through fingerprints (SHA256)’ as shown in the screenshot below.
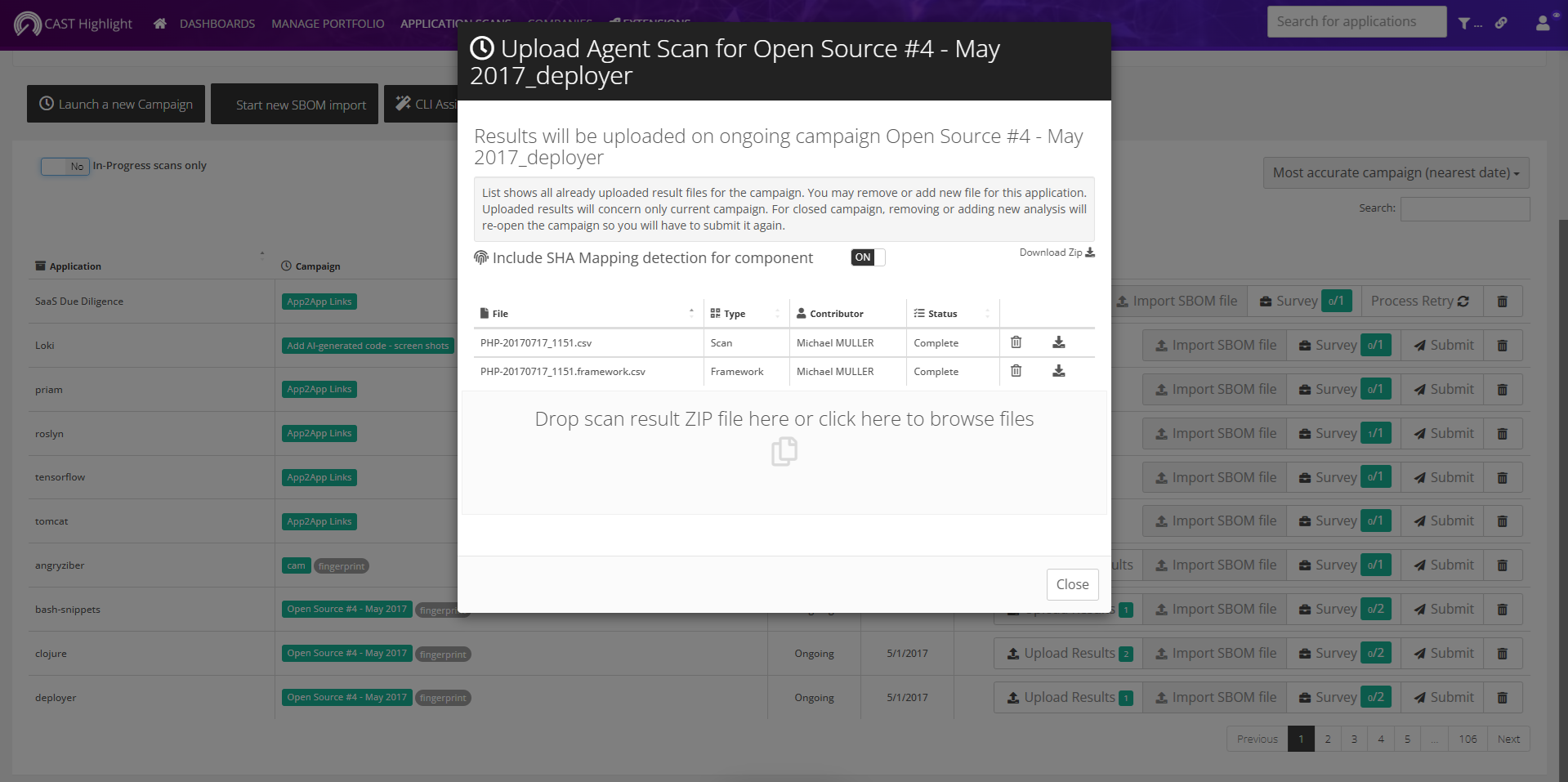
Note that you can also enable/disable this option after a scan, directly from the SaaS platform, when manually uploading the results. The APPLICATION RESULTS view indicates whether the option was enabled or not by displaying a ‘fingeprint’ tag for each code scan result. See below.