Feature Focus: CISA’s Known Exploited Vulnerability Insights
Traditionally, Common Vulnerabilities & Exposures (CVEs) maintained in the National Vulnerability Database (NVD) have been the primary source for tracking and managing known vulnerabilities in software. CVEs provide a standardized way to identify and categorize vulnerabilities, making it easier for organizations to assess their exposure to specific risks and take appropriate action. However, to better safeguard their applications, organizations should now extend their focus beyond CVEs and consider also using the Known Exploited Vulnerabilities (KEV) database provided by the Cybersecurity and Infrastructure Security Agency (CISA).
Using CISA’s KEV database is of paramount importance for several reasons, especially when dealing with open source components in applications:
- Real-world Exploitation Data: While CVEs provide essential information about vulnerabilities, they may not always include details on whether a particular vulnerability has been actively exploited in the wild. The KEV database, on the other hand, specifically focuses on vulnerabilities that are known to have been exploited. This real-world exploitation data is crucial for organizations as it helps them prioritize their remediation efforts. By addressing vulnerabilities that are actively targeted by malicious actors, organizations can reduce their risk of falling victim to attacks.
- Comprehensive Vulnerability Coverage: CVEs are comprehensive in their coverage, but the KEV database provides an additional layer of insight. It focuses on vulnerabilities that have been proven to be exploitable, offering a more practical perspective on the severity of a vulnerability. This ensures that organizations are not only addressing potential threats but also vulnerabilities that have demonstrated real-world impact.
- Timely and Actionable Information: The KEV database is known for its timely updates, ensuring that organizations receive information about newly discovered vulnerabilities that are actively being exploited. This timeliness allows organizations to react quickly, implementing patches or mitigations to protect their applications and data.
- Risk Mitigation: Integrating KEV data into your software security practices can help you make informed decisions about which vulnerabilities to prioritize for remediation. By focusing on vulnerabilities with a known history of exploitation, organizations can allocate their resources more efficiently, reducing the attack surface and minimizing the likelihood of security incidents.
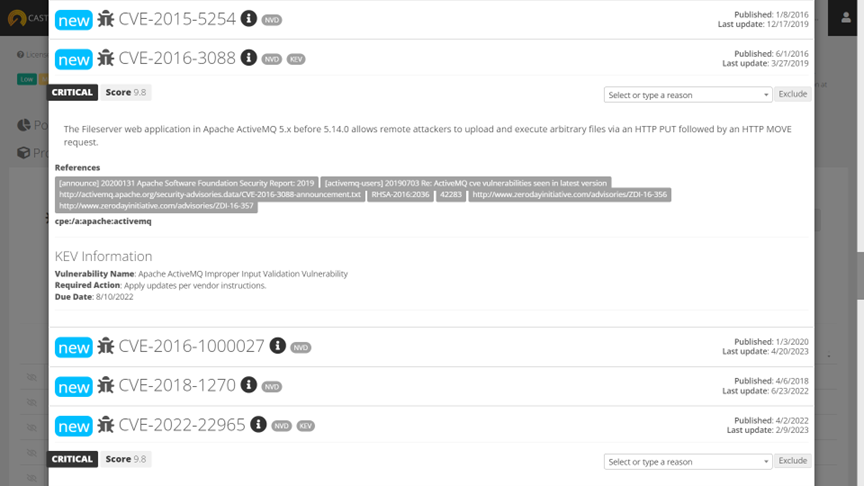
CAST Highlight now integrates KEV vulnerabilities by refreshing the vulnerability information every hour. For a given vulnerability detected for a given component version, a ‘KEV’ tag is added if this CVE is also part of the KEV database (i.e., has been exploited in the real world). To view this information in CAST Highlight, expand the vulnerability record to see detailed KEV information:
- Vulnerability name: completes what could be missing in the CVE record from NVD
- Required Action: gives a concrete actionable step when you have this vulnerability
- Due Date: this optional guidance for most of organizations – mandatory for U.S. agencies – gives a sense of urgency of a specific vulnerability to be remediated
You can also get this KEV information from the API, at both portfolio and application levels.
- Portfolio Level: POST {serverUrl}/WS2/domains/{domainId}/vulnerabilities
- Application Level: GET {serverUrl}/WS2/domains/{domainId}/applications/{applicationId}
The returned JSON will look like this:
"cisaVulnerability": {
"cveID": "CVE-2020-1938"
"vendorProject": "Apache",
"product": "Tomcat",
"vulnerabilityName": "Apache Tomcat Improper Privilege Management Vulnerability",
"dueDate": "2022-03-17",
"dateAdded": "2022-03-03",
"shortDescription": "Apache Tomcat treats Apache JServ Protocol (AJP) connections as having higher trust than, for example, a similar HTTP connection. If such connections are available to an attacker, they can be exploited.",
"requiredAction": "Apply updates per vendor instructions.",
"notes": ""
}
