CAST Highlight SAML/SSO Integration with Identity Providers (IdP)
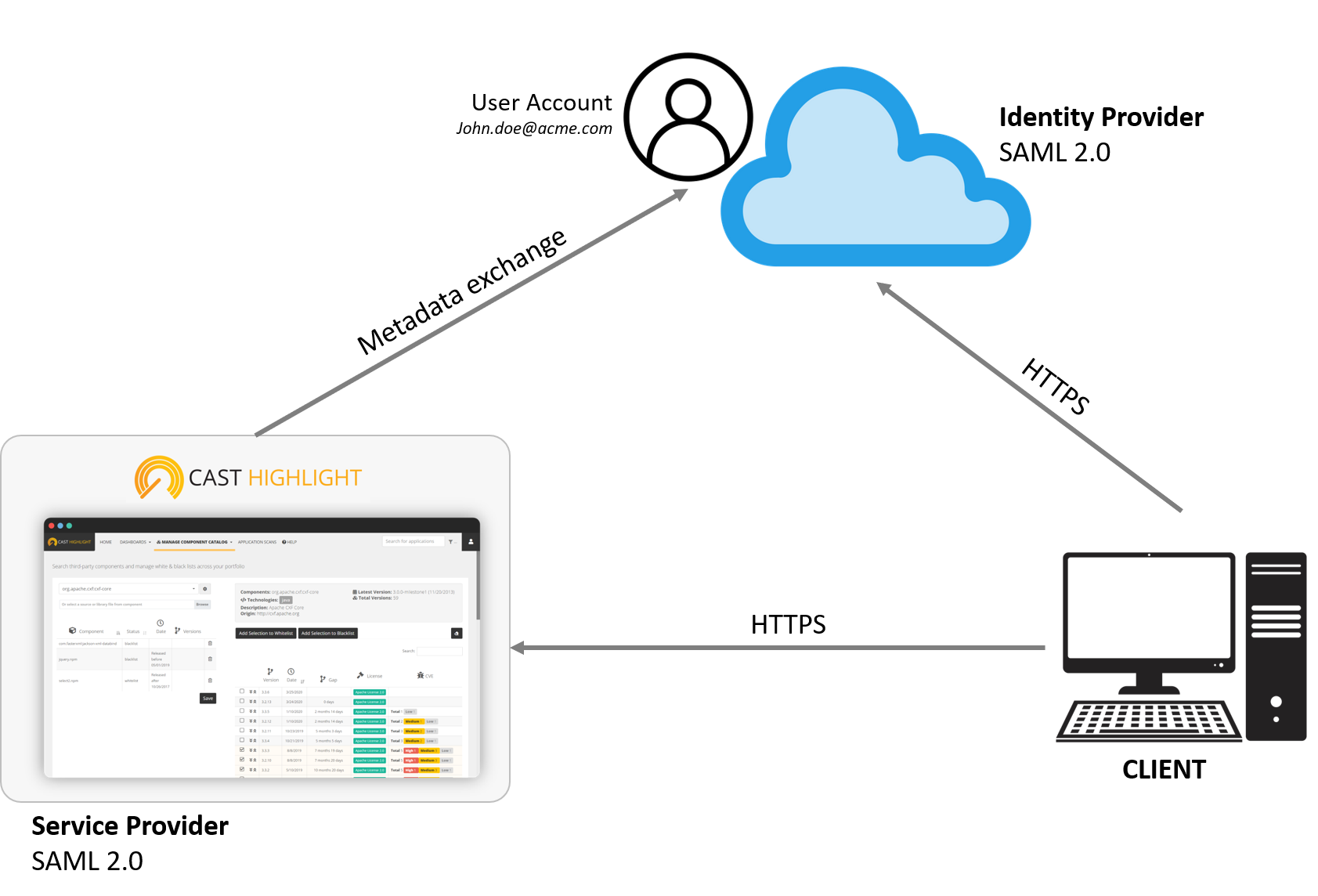
CAST Highlight supports SAML 2.0 which enables user authentication & role management from your Identity Provider (IdP).
To implement CAST Highlight’s user authentication using your SAML/SSO solution, you’ll need to have an active CAST Highlight user account with root-level access with a Portfolio Manager role and follow the documentation and steps described below.
SAML Setup with CAST Highlight
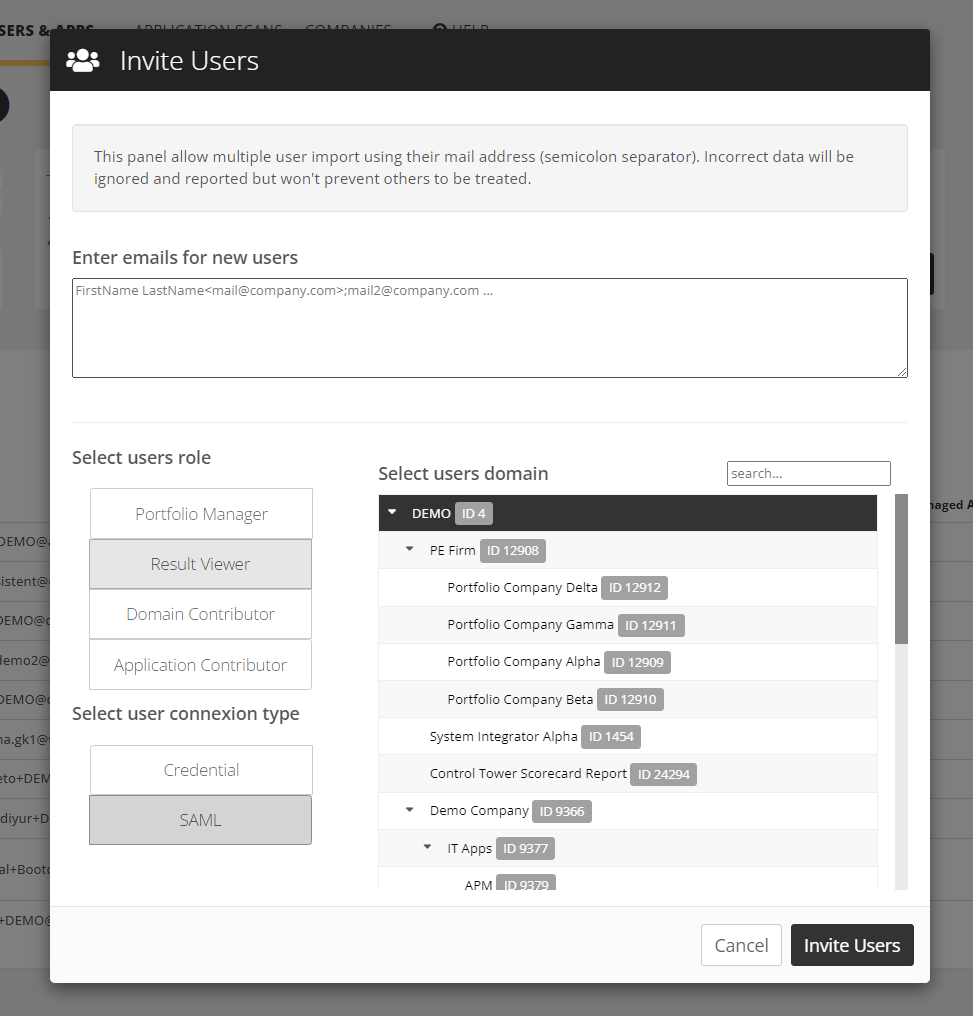
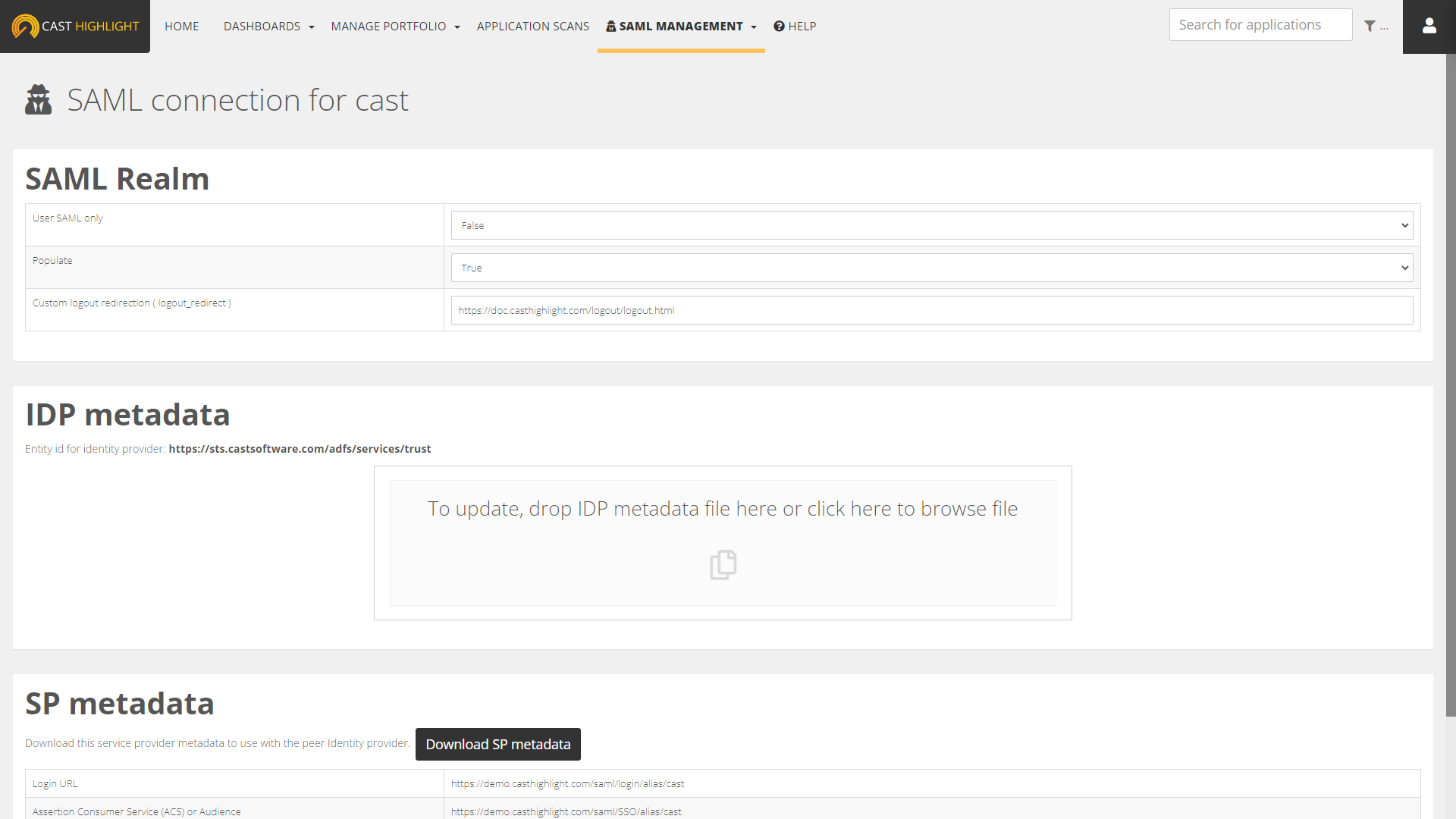
- As a Portfolio Manager of the CAST Highlight instance (root-level domain), go to COMPANIES > SAML Management
- Select the desired option for autorized user types for the company:
- User SAML only = False, to allow Portfolio Managers to invite both SAML and Credential users
- User SAML only = True, to allow Portfolio Managers to invite only SAML users
- Select the desired “Populate” option
- When ‘true’ is selected, users are automatically created in CAST Highlight, roles can be managed directly through CAST Highlight or from the IdP). This mode is highly recommended.
- When ‘false’ is selected, users must be created in CAST Highlight with the same e-mail address so that the user account can be transitioned to SAML. This mode is likely to be deprecated in the near future.
- Defined the redirection URL for logged out users (the page where users will be redirected after they log out from CAST Highlight)
- Upload the IdP metadata.
As soon as you uploaded the metadata and saved the configuration, CAST Highlight allows you to:
- See what will be the SAML login URL and the ACS (Assertion Consumer Service)
- Download the SP metadata that will be required by your IdP
Note: If you switch from an IdP to another, it is recommended to have a credential user account in order to being able to download the SP Metadata after the switch occured.
SAML Advanced Configuration
CAST Highlight currently supports two deployment modes for SAML/SSO.
| BASIC (User Authentication Management) | FULL (User Authentication & Permission Management) |
|---|---|
| By default, SAML will only manage the authentication of users. The other attributes (First name, Last name, Role) will be managed through CAST Highlight’s interface. |
This mode enables the customer to manage User information, Authentication, CAST Highlight Role, Subdomain from their IdP (Identity Provider).
|
| Pros: The Portfolio Manager can manage the user rights directly in the application (MANAGE PORTFOLIO > Manage Users) | Pros: Nothing needs to be done on CAST Highlight side, and when the user logs for the first time, everything is already configured and is working properly.
This mode is the only way to manage the level of the portfolio (subdomain) where the user will be attached to.
|
| Limitations: In this mode, the user can be created only at the root-level domain of the company portfolio (i.e., users can’t be attached to a subdomain, they will need to be edited by a Portfolio Manager from the Portfolio Management screen). | Limitations:
|
- Identity provider (IdP) = The service at client-side that manages SAML
- Service provider (SP) = The CAST Highlight application
SAML attributes
| IdP manages | Attribute name | SAML Basic | Value (type) |
|---|---|---|---|
| User Authentication (Claim) | NameID | Mandatory | email@domain.com (String) |
SAML attributes
| IdP manages | Attribute name | SAML Full | Value (type) |
|---|---|---|---|
| User Authentication (Claim) | NameID | Mandatory | email@domain.com (String) |
| User FirstName | hl.firstname | optional | FirstName (String) |
| User LastName | hl.lastname | optional | LastName (String) |
| User Role | hl.role | optional | Must contain one of these value:
|
| Sub-Domain User access rights | hl.subdomain | optional | (integer)
Note: hl.subdomain attribute should not be present if the user is attached to multiple domains for the same portfolio. |
Implementation
| Step # | Who | What | Comments |
|---|---|---|---|
| 1 | Customer | The customer must provide to Cast:
|
Most of the time the Entity_ID is the IDP url “sts.company123.com“, but Cast will retrieve it from the IdP Metadata file provided.
Claim:
SAML attributes:
|
| 2 | Customer | The customer must send one of the four Saml value of the attribute hl.role
How our customers manage this value ? Most of the time, our customer creates four AD/LDAP groups that are sent as attribute *. A user MUST be a member of only one role (one AD/LDAP group) |
Role attribute is case sensitive *:
|
| 3 | CAST | Cast integrates the IDP_metadata file and the Company_ID in the system, and provide the Service Provider (SP) metadata file to the customer
The customer integrates it in its system to finalize the configuration (SAML Secure Hash algorithm = SHA-256) |
Cast will provide these URLS:
Login (Sign on URL) : Assertion Consumer Service (ACS) or Audience: > https://{server}/saml/SSO/alias/<company123> |
| 4 | Customer | The customer can test the access to Highlight using the link provided by Cast (the one that contains “login”): https://{server}/saml/login/alias/<company123> |
Both IDP-initiated and SP-initiated are supported by CAST Highlight |
Here is the regex patterns that control the role in the AD group provided to hightlight “^.*(portfolioManager|applicationContributor|domainContributor|resultViewer).*$”
so that the customer can create a group like “gp.security.applicationHighlight.portfolioManager.users”
Each user must be only part of one Highlight_role AD_group
User Workflow
The invited user will receive an email with a link to the SSO login page. Once authenticated for the first time, the CAST Highlight user account will be automatically activated.
For further authentication, the user will be able to login from the login screen. Once the email address is provided, the user will be automatically redirected to the SSO login page.
Notes:
- The user won’t be able to change his password as this information is managed by your IdP
- API and CLI accesses must use a classic CAST Highlight user account with credentials
- The user must already exist on the customer AD/LDAP
- The user must have a CAST Highlight role defined (hl.role)
- Every attributes should be provided by the customer IdP
Nothing more to do here. The IdP will be master of data as the SAML attributes will always overwrite the user data stored in CAST Highlight.