Installation instructions for the CAST Highlight Cloud Maturity extension for Visual Studio Code
Download & Install Visual Studio Code
If VS Code is already installed, please skip to the next step. If not, you can download and install Visual Studio code here: https://code.visualstudio.com
Download & Install the extension
You can download and install the extension from the Visual Studio Code marketplace.
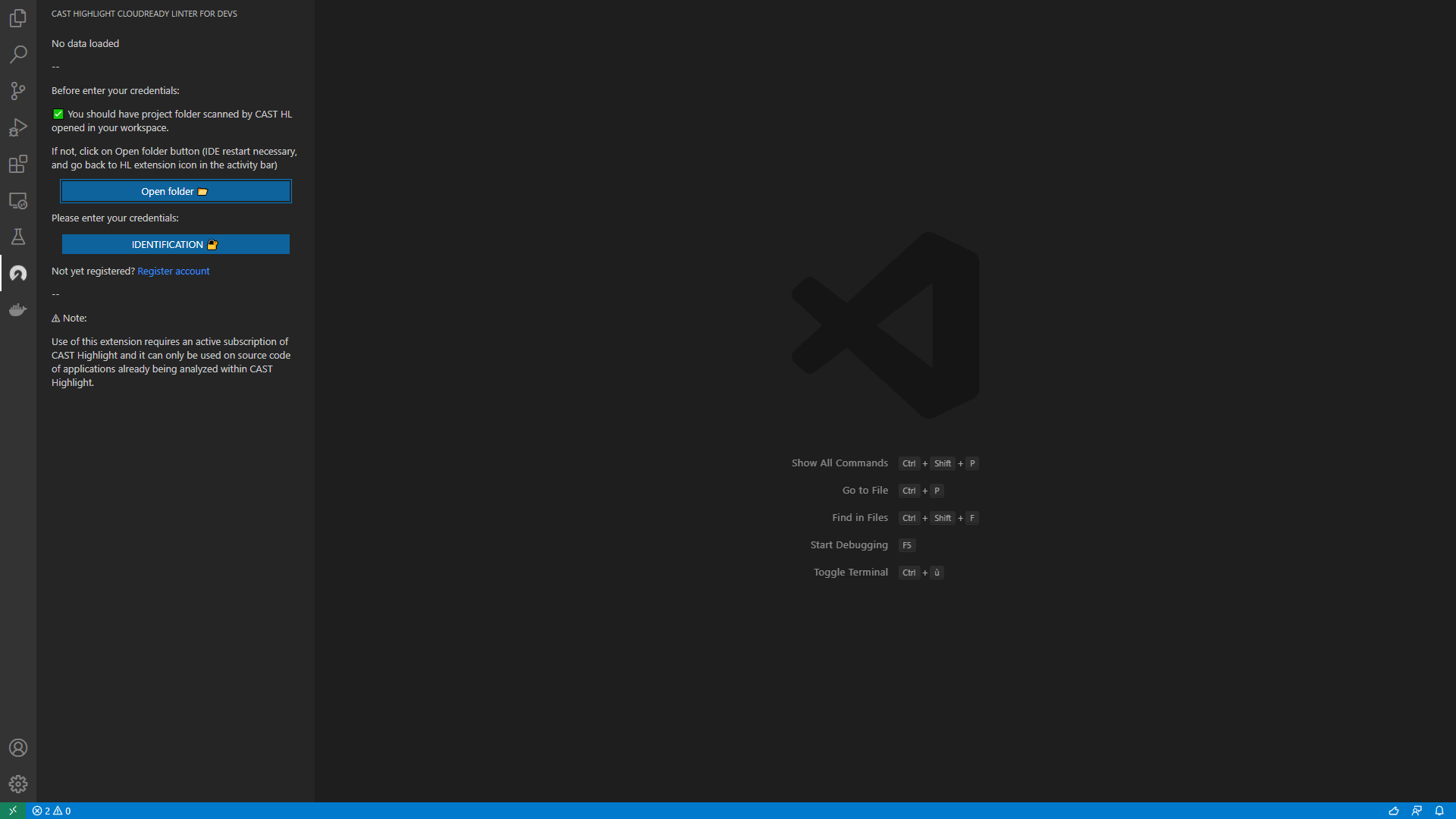
Create your CAST Highlight VS Code user account
In order to use the Cloud Maturity VS Code extension, you will need to create your personal user account. Simply click on “Register Account Here” in the extension window and follow the instructions (don’t forget to locate your CAST Highlight company identifier as it will be required to activate your access).
Once your account creation request has been submitted, you will receive an e-mail from CAST Highlight to verify your e-mail address. Click on the activation link to confirm your email address. The CAST team will validate your CAST Highlight subscription and activate your account for the VS Code extension within two days.
To access your account information in the future, visit this site and login: https://doc.casthighlight.com/vscode
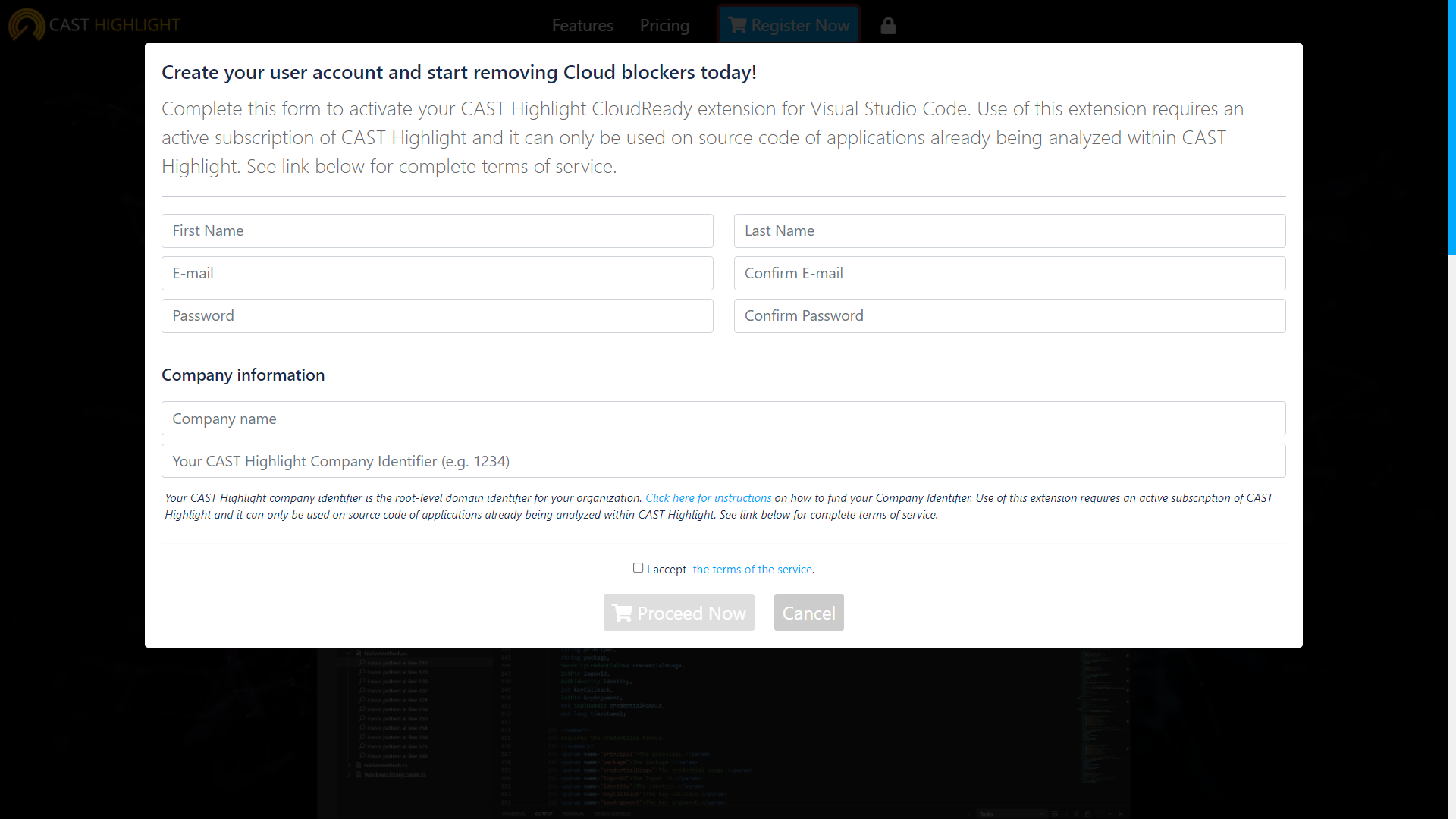
Sign in and load detail Cloud logs
You now have an active user account for the extension. Follow the three steps below to start identifying Cloud Blockers directly in VS Code.
- Open your workspace: click on “Open Folder” button to select the folder for your project. It should use the same folder structure that has been previously scanned by the CAST Highlight command line (refer to the section below on how to produce detailed scan logs required by the Cloud Maturity VS Code extension).
- Login with your credentials: click the “Identification” button and type your login/password
- Load the detailed CAST Highlight scan logs: click on “Load CAST Highlight Log file’” and select the CAST Highlight detailed scan logs. Logs are available for each scanned technology (e.g. cloudDetail_Java.csv)
- You’re now ready to navigate the source code files for your workspace and identify Blocker occurrences.
How to generate CAST Highlight scan logs with the command line
The CAST Highlight Cloud Maturity extension for VS Code reads detailed scan logs which contain Cloud Blocker information (Roadblocks, line numbers and positions, etc.).
These detailed scan logs (see below example) are produced by the CAST Highlight command line with the following option:
--dbgMatchPatternDetail
The logs are produced in the same folder as other scan result CSV files: {scannedFolder}/HLTemporary/analysis/cloudDetail_{technology}.csv
[CS] Scan Tue Dec 7 16:20:56 2021 [dir project] C:\mongo-csharp-driver-master/ Alert;Path;LineNumberPos;Url_doc "Perform Directory Manipulation";mongo-csharp-driver-master/src/MongoDB.Driver/Encryption\MongocryptdFactory.cs;20[0,16]|128[50,66];https://doc.casthighlight.com/Cloud Maturity_Directory_Manipulation_Practice?auth=977d0e61c5d240f729856db9d227aaf5 "Perform File Manipulation";mongo-csharp-driver-master/tests/MongoDB.Bson.Tests/IO\BsonBinaryReaderTests.cs;18[0,16]|82[20,31];https://doc.casthighlight.com/Cloud Maturity_File_Manipulation_Practice?auth=7d30ba0f5aeddf312a92a715c1038f24 "Perform File Manipulation";mongo-csharp-driver-master/src/MongoDB.Driver.Legacy/GridFS\MongoGridFS.cs;17[0,16]|531[35,46]|544[35,46]|568[35,46];https://doc.casthighlight.com/Cloud Maturity_File_Manipulation_Practice?auth=7d30ba0f5aeddf312a92a715c1038f24 "Use of an unsecured data string";mongo-csharp-driver-master/tests/MongoDB.Driver.Legacy.Tests\SystemProfileInfoTests.cs;102[-];https://doc.casthighlight.com/Cloud Maturity_Use_Unsecured_Data_Strings?auth=a95df2c7851bf5dcfb8be6009c92e05a "Use of unsecured network protocols (HTTP, FTP)";mongo-csharp-driver-master/tests/MongoDB.Driver.Tests/GeoJsonObjectModel\GeoJsonLinkedCoordinateReferenceSystemTests.cs;28[65,92]|38[65,92];https://doc.casthighlight.com/Cloud Maturity_Use_SecuredProtocols?auth=5af9b0822489b03c906db6b3d0009afe "Use of unsecured network protocols (HTTP, FTP)";mongo-csharp-driver-master/tests/MongoDB.Bson.Tests/Serialization/Serializers\NetPrimitiveSerializerTests.cs;1766[28,48];https://doc.casthighlight.com/Cloud Maturity_Use_SecuredProtocols?auth=5af9b0822489b03c906db6b3d0009afe "Using Crypto API";mongo-csharp-driver-master/src/MongoDB.Bson/Serialization/IdGenerators\AscendingGuidGenerator.cs;20[0,34];https://doc.casthighlight.com/Cloud Maturity_Use_Crypto_API?auth=83196fa77e7a35409d833d7b4cc41b16 "Using Crypto API";mongo-csharp-driver-master/src/MongoDB.Driver.Core/Core/Authentication\AuthenticationHelper.cs;20[0,34];https://doc.casthighlight.com/Cloud Maturity_Use_Crypto_API?auth=83196fa77e7a35409d833d7b4cc41b16 "Using New Process in System.Diagnostics namespace";mongo-csharp-driver-master/src/MongoDB.Driver/Encryption\MongocryptdFactory.cs;19[0,25]|210[37,49];https://doc.casthighlight.com/Cloud Maturity_Use_Sub_Processes?auth=cba316edded10277296df36ccd2fae09 "Using file system";mongo-csharp-driver-master/tests/MongoDB.Bson.Tests/IO\CStringUtf8EncodingTests.cs;53[20,29]|54[20,29];https://doc.casthighlight.com/Cloud Maturity_Use_File_System?auth=b1fede2ca6e441c908b1f4563b375e0c "Using hardcoded network IP address (IPV4, IPV6)";mongo-csharp-driver-master/tests/MongoDB.Driver.Core.Tests/Core/Clusters\ClusterDescriptionTests.cs;387[104,113];https://doc.casthighlight.com/Cloud Maturity_Use_Hardcoded_IP_Address?auth=a6ab8fb4f9ec7a7c7452a9df1d0eef2f "Using system DLLs";mongo-csharp-driver-master/src/MongoDB.Driver.Core/Core/NativeLibraryLoader\DarwinLibraryLoader.cs;57[12,23]|60[12,23];https://doc.casthighlight.com/Cloud Maturity_Use_OS_Dependency?auth=c3085dd64ed56376c64524d05272de5d "Using system DLLs";mongo-csharp-driver-master/src/MongoDB.Driver.Core/Core/NativeLibraryLoader\LinuxLibraryLoader.cs;57[12,23]|60[12,23];https://doc.casthighlight.com/Cloud Maturity_Use_OS_Dependency?auth=c3085dd64ed56376c64524d05272de5d